Edge computing security risks and solutions
As we have learned from the whitepaper 'Edge Computing in Industrial Environment' about the overview and different forms of Edge computing, we will discuss more on various Edge computing security risks and their solutions.
Edge computing in IIoT satisfies the real-time needs for lightweight intelligent manufacturing whilst also increasing network agility and security. Cyberattacks compromise the confidentiality, integrity, or availability of data, as well as to disrupt a company's activities. Vulnerable network appliances, such as edge devices, continue to be one of the most effective attacks. They are a frequent target for attackers wishing to get inside, due to their position and functions which provide interconnectivity between different networks with the transmission, monitoring, filtering, translating, or storing of the data that passes from one network to another. Once a threat actor gains access to an edge device, they can launch attacks that can cause operational downtime, data theft, financial loss, and reputational damage.
The ‘security category’ comprises of wireless network security challenges, authentication and trust challenges, access control, and intrusion detection. Edge computing takes advantage of several different technologies to build the network, introducing potential to several attacks, such as man-in-the- middle, distributed denial of service (DDoS), side-channel attacks, device hijacking, malware injection attacks, authentication / authorization attacks and permanent denial of service (PDoS). A DoS (Denial of service) attack, is when a compromised system attempts to flood a resource to purposefully overload it, and a Distributed DoS or DDOS is when multiple compromised systems are orchestrated to do the same. Whenever a malicious packet is identified, it will be dropped before reaching its target.
There are four main categories of edge devices that help connect and secure enterprise or service provider networks. They are - Network edge devices (routers, switches, wide area network devices, VPN concentrators), Network security devices (firewalls), Network monitoring devices (network based intrusion detection systems) and Customer premise devices (integrated access devices). The system vulnerabilities are determined by the system's security layers and security techniques. The table below shows the four security levels of the IoT information system paradigm as well as the security measures used. The most susceptible layer is network security, whereas data security is the most secure.
| No. | Security layers | Security methods |
|---|---|---|
1 | Network security | Authorization monitoring, egress filtering, network firewall, routing protocols security |
2 | Device security | Authentication control, patch management, tamper proofing, intrusion detection system |
3 | Application security | Application firewall, software development life cycle security, biometric authentication |
4 | Data security | Access control, cryptographic algorithms, data encryption, routing protocol security |
Security issues exist on edge devices, whether they are managed by end users or administrators. Moving data processing closer to the network edge has security implications. A few of the Edge Computing Security Risk are - Malicious Hardware/Software Injections, Physical Tampering & Attacks, Routing Information Attacks, Data storage, backup and protection risks, Password and authentication risks, Perimeter defense risks, Cloud adoption risks.
Security-as-a-Service (SECaaS) at the Network Edge
The deployment of security instances in remote data centers has several drawbacks, in order to overcome these issues, Edge Computing offers the opportunity to efficiently host services at the network edge, and provides remarkable benefits in terms of shortening latency and traffic reduction. As shown in below figure the Security-as-a-Service in industrial edge scenarios, the provisioning of on-demand security services according to the SECaaS model is gaining notable attention from both industrial and research communities. On the other hand, the limited capabilities of an edge node introduces potential constraints in the overall management.
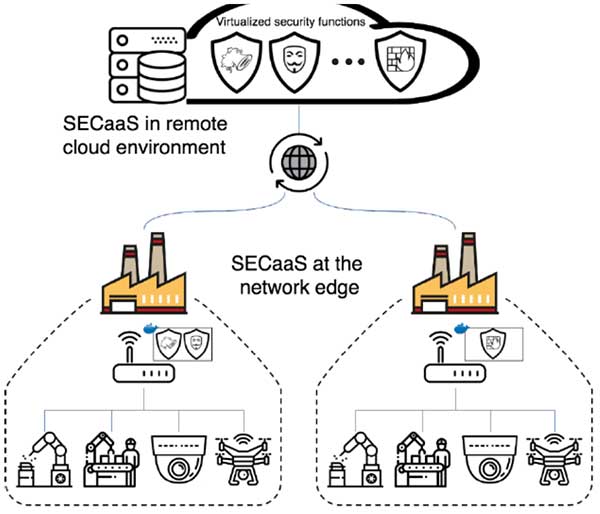
Figure: Security-as-a-Service in industrial edge scenarios
Implementing solutions
Edge computing is considered a secure computing paradigm as long as effective cybersecurity practices are in place throughout the network. The best practices for edge computing security are to use access control and surveillance, establish audit procedures to control data and application hosting, control edge configuration and operation from central IT operations, apply the highest level of network security, treat the edge as a part of the public cloud portion, monitor and log all edge activity.
In order to reinforce the security in the smart things, sensors/devices shall provide two distinct operating modes: configuration mode and service mode. The first one allows configuration actions such as the modification of operating parameters (e.g. signal strength, cryptographic keys, network address, authentication method) and updating of the firmware, amongst others. The latter one is the common operating mode in which the smart thing does what it is intended to do and allows data to be collected. As a security measure, the smart thing shall use an access control method before switching modes, such as validating a PIN (Personal Identification Number).
Machine learning approach:
There is lot of benefits by using machine learning and deep learning approaches to identify DDOS attacks, with some basic machine learning techniques such as Bayes and Bayesian network classifiers being used to effectively detect botnet DDOS attacks. Using a basic auto-encoding method, a deep learning model can be used to detect encrypted DDOS traffic. DDOS attacks may also be detected using neural networks. For learning/training purposes, many learning-based detection techniques require a substantial volume of DDOS traffic, which can only be obtained after the edge servers have been exposed to the attacks, better security framework is much needed to fully adopt an edge computing platform.Lightweight virtualization:
The use of the virtualization technology within the edge computing platform also introduces potential security threats, such as virtual machine (VM) hopping or eavesdropping. New challenges are introduced in the deployment of service instances at the network edge. Especially when considering resource-constrained edge nodes, lightweight virtualization technologies are strictly required. In this regard, Docker containers represent a promising platform for Edge Computing, multiple devices can collaboratively perform security functions, providing value-added service benefits.Hardware and Software Security Methods:
To avoid the security vulnerabilities for software or hardware, it is necessary to ensure that each update file is encrypted using a cryptographic method that updates files transmitted over the encrypted environment and that the update files do not reveal important user information. Also, it is necessary to ensure that IoT information system upgrades have been revised, verified and installed in safe boot mode, before being sent and applied.Stay connected with our other inspired blogs where we have discussed about different forms of Edge computing like Thick, Thin and micro-edge solutions, Integration of Edge computing in PACs and PLCs, Edge computing deployment strategies and IEEE standards.
Stay informed
Keep up to date on the latest information and exclusive offers!
Subscribe now
Thanks for subscribing
Well done! You are now part of an elite group who receive the latest info on products, technologies and applications straight to your inbox.






